CVE-2023-20248
Stored Cross-Site Scripting vulnerability in "Video address" parameter
5.4 (Medium)
CVSS:3.1/AV:N/AC:L/PR:L/UI:R/S:C/C:L/I:L/A:N
Cisco TelePresence Management Suite
Earlier than 15.13.6
Jakub Sajniak (@kubolos231), Stanislaw Koza
The vulnerability in the web-based management interface of Cisco TelePresence Management Suite (TMS) Software could allow an authenticated, remote attacker to conduct a cross-site scripting (XSS) attack against a user of the interface. This vulnerability is due to insufficient input validation by the web-based management interface.
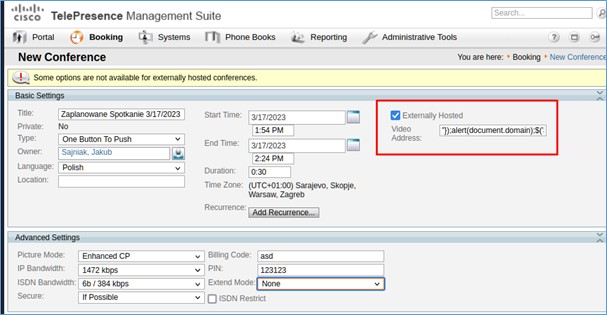
An attacker could exploit these vulnerabilities by string termination injection in a script block inside the video address parameter of the new conference. A successful exploit could allow the attacker to execute arbitrary script code in the context of the affected interface or access sensitive, browser-based information.
Cisco has released software updates that address this vulnerability. There are no workarounds that address this vulnerability.
- Login to CMS app with the Operator access
- Navigate to „Booking -> New Conference”
- Check „Externally Hosted”, and in the „Video address” field enter the following string:
"});alert(document.domain);$('STM').keyup(function(){//
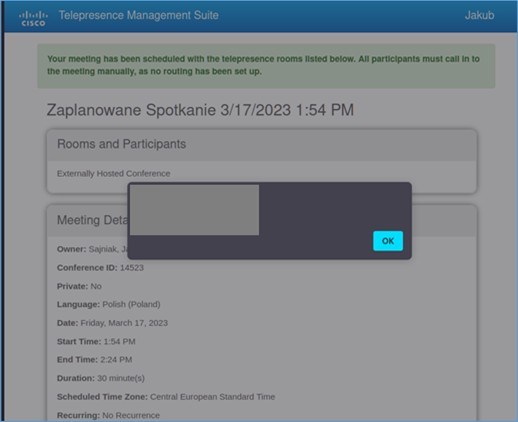
- Click on „Save Conference” button and then „Meeting Details” button
- 24-04-2023 - Vulnerability reported to vendor
- 24-04-2023 - First response from Cisco to percise versions tested
- 27-07-2023 - Successful reproduction of the vulnerability by Cisco
- 11-01-2024 - Security advisory is published by Cisco