CVE-2020-4632
Server-side request forgery
5.7 (Medium)
CVSS:3.1/AV:A/AC:L/PR:L/UI:N/S:U/C:N/I:H/A:N
IBM InfoSphere (Metadata Asset Manager)
11.7.1
Maciej Kaczorowski
IBM InfoSphere Metadata Asset Manager is vulnerable to server-side request forgery. A remote authenticated attacker could exploit this vulnerability to submit or control server requests by sending a specially crafted request.
Steps to reproduce:
- Go to the module Metadata Asset Manager and log in as an administrator,
- Go to tab: Administration -> Metadata Interchange Servers,
- Click on the „New” button,
- In the „Name” field, enter any string of characters, for example: „SSRF test”,
- In the „Host” field: enter hostname or IP, which you want to scan,
- In the „Agent HTTPS port” field, enter a port number, which you want to scan,
- Go to tab „Import”, then click on the „New Import Area” button,
- Select the previously created resource from the drop-down list next to the „Metadata interchange server” („SSRF test”) field,
- If the port is open, the application will return SSL exception error (see Picture 1),
- If the port is closed, the application will return connection error (see Picture 2).
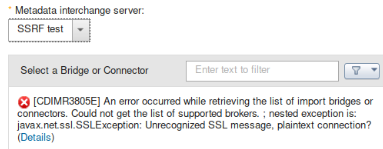
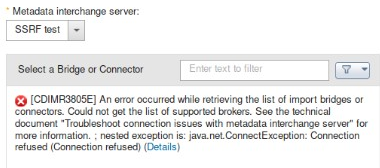
- 25-01-2020 - Vulnerability reported to the vendor
- 25-01-2020 - First response from the vendor
- 13-07-2020 - Vulnerability acknowledged by the vendor
- 03-09-2020 - Advisory published by IBM
- 03-09-2020 - Public disclosure
- 25-11-2021 - The PoC release
